In today’s complex and distributed IT environments, securing infrastructure and applications can be an overwhelming challenge. With distributed networks spanning data centers, multi-cloud, hybrid cloud, and edge infrastructure, traditional network security approaches often fall short. This is where Hashicorp Boundary Enterprise Keygen comes in.
An Introduction to Boundary Enterprise
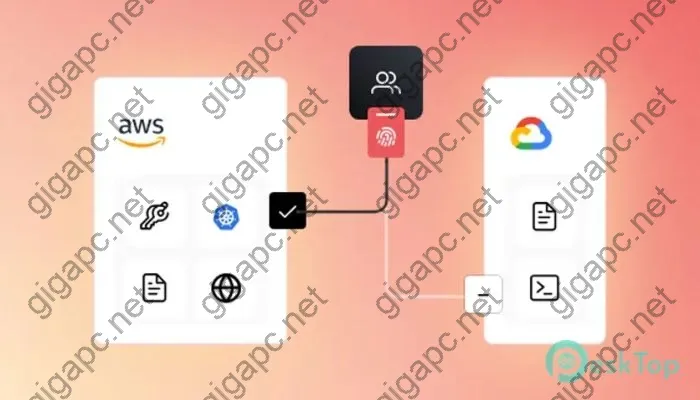
Hashicorp Boundary Enterprise Download free is a modern security solution purpose-built for dynamic, distributed enterprise environments. It takes a unique approach called “network identity” security that connects security directly to application services and infrastructure, rather than traditional IP network constructs. This allows Boundary Enterprise to provide consistent security across any type of infrastructure – on-prem, multi-cloud, hybrid cloud, containers, serverless, and more.
Some key capabilities and benefits of Hashicorp Boundary Enterprise Keygen include:
-
Simplified Security for Dynamic Infrastructure – Boundary Enterprise works across any infrastructure environment and adjusts security automatically as underlying infrastructure changes. This eliminates complex network security constructs like VPNs, ACLs, and firewall rules that have to be constantly updated.
-
Consistent Access Controls – Boundary Enterprise uses role-based access controls, multi-factor authentication, and other identity-centric mechanisms to govern access to infrastructure and applications. These controls persist regardless of where apps and infrastructure are deployed.
-
Micro-segmentation – Boundary Enterprise makes micro-segmentation easy by connecting security directly to each application service rather than the network. This reduces lateral threat movement and enables precise access controls.
-
Insider Threat Protection – Role-based controls, behavioral monitoring, and application-layer monitoring helps Boundary Enterprise detect and prevent malicious insider activities across infrastructure.
-
Extensive Auditing – Detailed logs provide complete visibility into user activities for security forensics, compliance, and auditing requirements.
In short, Hashicorp Boundary Enterprise Free download takes the complexity out of securing modern, dynamic environments by aligning security directly to applications rather than fluctuating network constructs.
Challenges Secured by Boundary Enterprise
Hashicorp Boundary Enterprise Keygen helps organizations address several key security and compliance challenges, including:
Multi-Cloud Security
Multi-cloud adoption is accelerating rapidly as organizations implement hybrid and multi-cloud strategies. However, this brings major security and governance challenges. Boundary Enterprise secures multi-cloud in a unified way by:
- Extending consistent identity and access controls across on-prem, public cloud, and hybrid cloud infrastructure
- Limiting lateral movement between cloud environments
- Enforcing least privilege access and just-in-time elevation
- Protecting cloud management plane access
This helps organizations gain visibility and control across diverse cloud environments from a single security solution.
Dynamic Application Environments
Modern application environments like containers, serverless, and orchestrators enable more rapid delivery but also increase complexity for security teams. Full version crack Hashicorp Boundary Enterprise simplifies this by:
- Auto-discovering infrastructure and applications
- Applying consistent controls as environments change
- Embedding security directly into app delivery pipelines
- Limiting lateral movement across containers and functions-as-a-service
As a result, security can keep pace with rapid application changes instead of getting in the way.
Privileged Access Management
Controlling privileged access is crucial for reducing risk. Boundary Enterprise prevents privilege abuse by:
- Automatically discovering privileged accounts
- Applying just-in-time elevation of privileges
- Recording all privileged user activities for auditing
- Alerting on suspicious privileged behaviors
This reduces standing privileges while still enabling critical functions.
Hashicorp Boundary Enterprise Keygen protects across a wide range of other use cases as well including DevOps pipelines, stoping ransomware, segmenting networks, and more.
See also:
Core Capabilities
Hashicorp Boundary Enterprise Full version crack secures environments using core capabilities focused on network identity, insider threat detection, and privileged access management.
Network Identity Fabric
The Boundary Network Identity Fabric connects security directly to application infrastructure through agents and proxies. This creates a flexible identity-based network overlay organizations can use to enforce consistent security spanning any environment.
Key elements of the Network Identity Fabric include: * Hosts and Targets – These are secured application infrastructure like servers, containers, cloud services, etc. Hosts run Boundary agents to handle authentication and authorization. * Proxies – Proxies manage site-to-site connectivity between different Boundary Fabrics. * Controller – The Controller provides central management and intelligence across the Fabric.
Combined, this forms a secure mesh overlay that extends security controls consistently across dynamic environments.
See also:
Insider Threat Detection
The Network Identity Fabric also equips Boundary Enterprise with extensive behavioral monitoring capabilities across distributed infrastructure. This allows detecting insider threats through analytics like:
- User activity monitoring – Tracking keystroke logging, process invocation history, and file accesses for anomaly detection.
- Host telemetry – Monitoring compute patterns, network flows, and file changes to uncover malicious activities.
Boundary stitches together high fidelity events across hybrid or multi-cloud environments into centralized monitoring and analytics. This makes it easy to spot suspicious privilege abuse, data exfiltration, or lateral movement attempts that would otherwise go undetected.
Just-In-Time Privileged Access
Boundary Enterprise also governs privileged access via just-in-time elevation coupled with extensive auditing. Instead of standing privileges, admins must authenticate through Boundary to obtain temporary elevation tokens granting privileged access.
All activities are logged centrally during privileged sessions for auditing and forensics. This enables safe privileged access while preventing standing privileges that attackers covet.
Implementation and Deployment Freedom
One other key benefit Download free Hashicorp Boundary Enterprise Keygen provides is deployment flexibility. Organizations can leverage various implementation options to best align with their requirements and preferences.
Deployment Models
Boundary supports flexible deployment options:
- On-Prem Data Center – Deploy controllers and gateways within internal data centers for on-prem protection.
- Managed SaaS – For cloud-first organizations, Boundary offers a managed SaaS delivery model removing the need to deploy infrastructure.
- Hybrid – For more complex environments, Boundary supports hybrid models combining on-prem and SaaS-delivered components.
This range of choice helps accommodate the needs of various organizations and infrastructure profiles.
See also:
Integration Ease
Hashicorp Boundary Enterprise Keygen also integrates readily with existing IT systems via APIs and lightweight collectors. Some examples include:
- Identity providers – Integrate with IdPs like Okta, Azure AD, LDAP servers for smoother user and policy management.
- Orchestrators – Sync infrastructure changes from Kubernetes, ServiceNow and other tools to maintain an up-to-date security posture.
- SIEMs – Pipe Boundary logs into SIEM platforms like Splunk and IBM QRadar to enrich security analytics.
Rather than introducing yet another siloed product, Boundary aims to be a flexible security control plane coordinating defenses across platforms.
And that provides a high level overview of how Free download Hashicorp Boundary Enterprise Keygen works to simplify security for modern enterprise environments! With its distributed Network Identity Fabric and identity-centric approach, Boundary Enterprise reduces the friction organizations often encounter when trying to govern complex and fluid infrastructure and applications.



The latest enhancements in update the newest are extremely cool.
The speed is a lot better compared to older versions.
It’s now much simpler to complete jobs and organize content.
The new enhancements in version the latest are extremely cool.
The program is truly amazing.
I absolutely enjoy the new dashboard.
The recent functionalities in update the latest are extremely helpful.
It’s now much more intuitive to complete tasks and track information.
It’s now a lot easier to complete tasks and track data.
It’s now a lot more user-friendly to complete projects and organize information.
It’s now far easier to complete jobs and manage content.
I absolutely enjoy the enhanced interface.
The speed is a lot enhanced compared to the original.
It’s now a lot more intuitive to get done jobs and organize data.
The new functionalities in update the newest are really cool.
The software is absolutely fantastic.
I would strongly endorse this software to anyone needing a powerful platform.
The latest updates in release the newest are so cool.
The tool is really impressive.
The software is definitely fantastic.
I appreciate the upgraded UI design.
The recent enhancements in version the newest are incredibly great.
I love the enhanced workflow.
The recent updates in release the latest are so great.
This software is definitely great.
I absolutely enjoy the upgraded interface.
I really like the upgraded dashboard.
The responsiveness is so much better compared to older versions.
It’s now much simpler to get done jobs and organize content.
It’s now far simpler to complete jobs and organize content.
I love the upgraded layout.
I would absolutely endorse this application to professionals wanting a robust product.
I appreciate the improved workflow.
The platform is truly great.
The recent updates in update the latest are so cool.
I absolutely enjoy the improved layout.
The performance is significantly enhanced compared to the original.
The speed is so much faster compared to the original.
The speed is significantly faster compared to last year’s release.
It’s now far simpler to do work and organize information.
The new enhancements in release the newest are incredibly useful.
This platform is really fantastic.
I appreciate the upgraded workflow.
I appreciate the upgraded layout.
The responsiveness is so much better compared to the previous update.